LDAP (Active Directory)
Overview
The On-premises Active Directory connector enables seamless integration with Microsoft Active Directory for user and group management. This connector allows Leena AI Agents to search, retrieve, create, update, and delete user accounts and groups within your on-premises AD environment, making it ideal for identity management and authentication workflows.
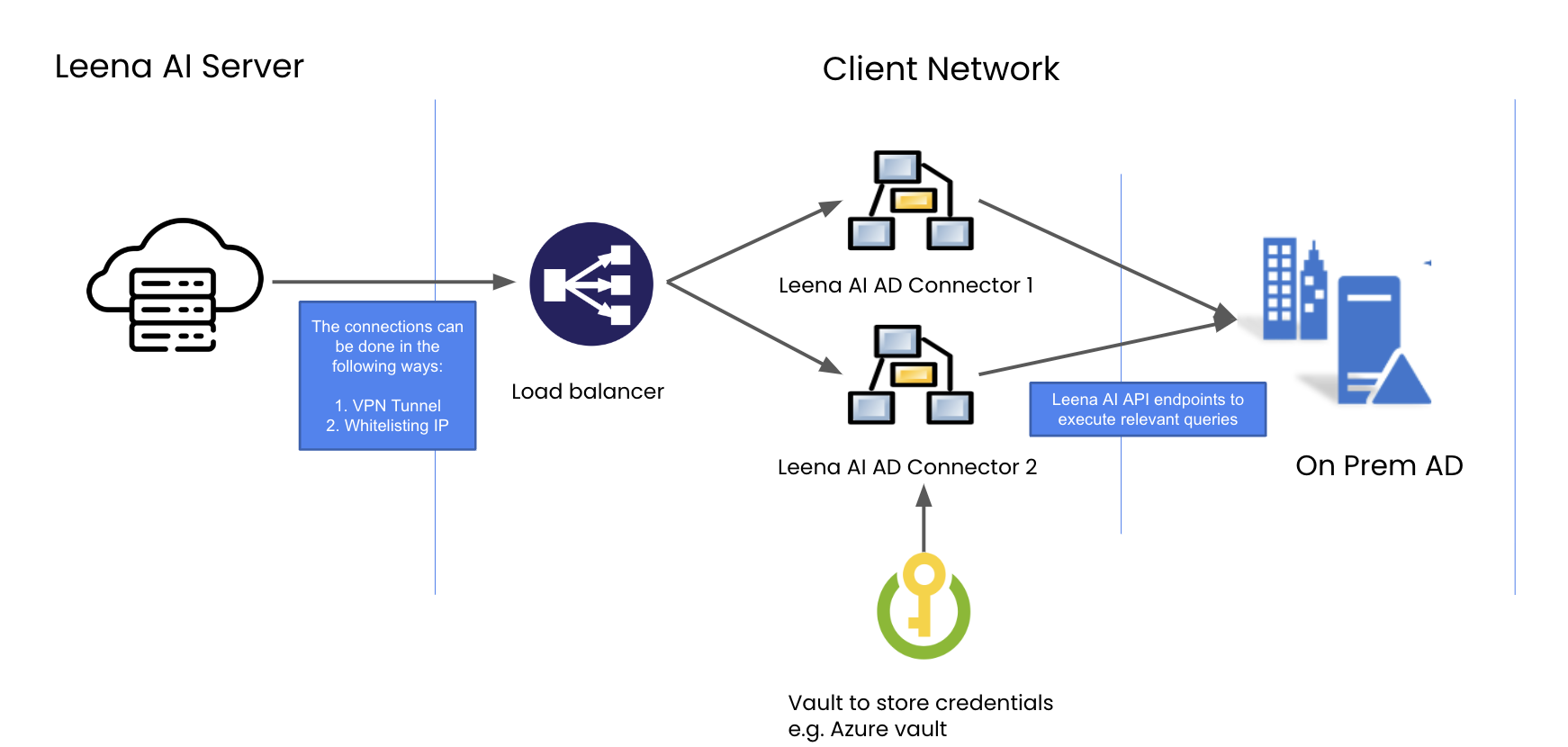
Leena AI utilizes an LDAP connector, seamlessly integrated within the same infrastructure as Active Directory.
API Details
Leena AI integrates with Active Directory via LDAP protocol.
Setup
On-premises Active Directory connections require secure domain credentials to access directory information.
Prerequisites
Before setting up the Active Directory connector, ensure you have:
Server Requirements for Deploying AD Connector:
- 2vCPUs
- 4 GB RAM
- Ubuntu
- Outbound internet access from the server (Initial setup & maintenance)
- SSL certificate
Active Directory Requirements:
- List of all the AD forests, domains and subdomains and their Private IPs and DN
- Credentials to authenticate/bind with the AD (need separate credentials if there are multiple forests and credentials vary for each forest), along with appropriate permissions to perform the listed actions
- Ability to connect to the server from Leena AI's side (either via IP whitelisting or via site-to-site VPN)
- Test users, groups etc to test the privileges
Get credentials
Add connection
Here is how to add a connection on Leena AI:
- Log in to your Leena AI workspace
- Navigate to Settings > Integrations
- Search for "Active Directory" and select it from the list to add its new connector
- Start configuring the connector
- Domain Controller: The hostname or IP address of the AD domain controller
- Port: The port number for the AD server (typically 389 for LDAP or 636 for LDAPS)
- Domain: The Active Directory domain name (e.g., "company.local")
- Username: The username with appropriate permissions to access AD
- Password: The password for the user account
- Use SSL: Boolean to indicate whether to use LDAPS (LDAP over SSL)
- Save the connector configuration
Actions
The following actions are supported for the LDAP/Active Directory connector:
Users: Create user
Creates a new user entry in the Active Directory. The Agent can leverage the skill (workflow), which has been designed to create a new user account in the directory, once the user raises a query to do so.
Input Parameters
Here are the input parameters required to set up this action:
Mandatory
| Name | Description |
|---|---|
| Parent distinguished name | The DN of the container where the user will be created (e.g., ou=Users,dc=example,dc=com) |
| Relative distinguished name | The RDN for the new user (e.g., cn=john.doe) |
Optional
| Name | Description |
|---|---|
| First Name (General) | The user's first name (givenName attribute) |
| Last Name (General) | The user's last name (sn attribute) |
| Display Name (General) | The display name for the user |
| Description (General) | A description of the user account |
| E-mail-Addresses (Mail) (General) | The user's email address |
| User Logon Name (Userprincipal Name) (Account) | The UPN for the user (e.g., [email protected]) |
| User Logon Name (Pre W2K SAM Accountname) (Account) | The pre-Windows 2000 logon name |
| User Account Control (Account) | UAC bitmask controlling account properties |
| Title (Organization) | The user's job title |
| Department (Organization) | The user's department |
| Company (Organization) | The user's company |
| Manager (Organization) | DN of the user's manager |
| Employee ID (Organization) | The user's employee ID |
| Telephone Number (Telephones) | The user's phone number |
| Mobile (Telephones) | The user's mobile phone number |
| Street (Address) | Street address |
| City (Address) | City |
| State/Province (Address) | State or province |
| Zip/Postal Code (Address) | Postal code |
| Country Name (Address) | Country |
Here is a sample JSON input:
{
"parentDn": "ou=Users,dc=example,dc=com",
"rdn": "cn=john.doe",
"entry": {
"givenName": "John",
"sn": "Doe",
"displayName": "John Doe",
"mail": "[email protected]",
"userPrincipalName": "[email protected]",
"sAMAccountName": "john.doe",
"title": "Software Engineer",
"department": "Engineering",
"company": "Example Corp",
"telephoneNumber": "+1-555-555-1234"
}
}Response
Upon successful creation, the action returns the operation status and details including:
- HTTP status code
- Operation result data
Users: Search user
Retrieves a list of users from the Active Directory. This action can be leveraged by Leena AI Orchestrator/Agent to search for users based on various criteria. Here are some common use cases:
- Employee Lookup: Find users by name, email, or employee ID
- Department Search: List all users in a specific department
- Manager Search: Find all direct reports of a manager
- Account Status Check: Search for users with specific account statuses
Input Parameters
Here are the input parameters required to set up this action:
Optional
| Name | Description |
|---|---|
| Base | The base DN to start the search from |
| Query Planner | Toggle to use the visual query builder (default: enabled) |
| Filter | Raw LDAP filter string (when Query Planner is disabled) |
| Operator | Filter operator type: Equality, Presence, Substring, Greater than equals, Less than equals, Approximate |
| Attribute | The LDAP attribute to search on |
| Value | The value to search for |
| Initial | Initial substring for substring searches |
| Any | Middle substring for substring searches |
| Final | Final substring for substring searches |
| Attributes | Array of attributes to return in the results |
Here is a sample JSON input:
{
"base": "ou=Users,dc=example,dc=com",
"queryPlanner": true,
"filterObject": {
"operator": "EQUALTITY",
"attribute": "department",
"value": "Engineering"
},
"attributes": ["cn", "mail", "title", "department", "manager"]
}Response
The action returns a list of user objects, each containing:
- Distinguished Name (DN)
- Requested attributes (e.g., common name, email, title)
- Any additional attributes specified in the search
Users: Modify user
Updates an existing user's attributes in Active Directory. The Agent can leverage the skill (workflow), which has been designed to modify user properties. Here are some common use cases:
- Profile Updates: Update contact information, job title, or department
- Role Changes: Modify organizational attributes when employees change roles
- Account Maintenance: Update account control settings
- Contact Information: Update phone numbers, addresses, or email addresses
Input Parameters
Here are the input parameters required to set up this action:
Mandatory
| Name | Description |
|---|---|
| Distinguished name | The DN of the user to modify |
Optional
| Name | Description |
|---|---|
| Replace | Array of attributes to replace with new values |
| Add | Array of attributes to add new values to |
| Delete | Array of attributes to remove values from |
| Delete JSON | JSON string for bulk delete operations |
Here is a sample JSON input:
{
"dn": "cn=john.doe,ou=Users,dc=example,dc=com",
"replace": [
{
"type": "title",
"values": "Senior Software Engineer"
},
{
"type": "department",
"values": "Platform Engineering"
}
],
"add": [
{
"type": "telephoneNumber",
"values": "+1-555-555-5678"
}
]
}Response
Upon successful modification, the action returns:
- HTTP status code
- Operation result data
Users: Delete user
Deletes an existing user from Active Directory. The Agent can leverage the skill (workflow), which has been designed to remove user accounts during offboarding. Here are some common use cases:
- Employee Offboarding: Remove accounts when employees leave
- Account Cleanup: Delete obsolete or duplicate accounts
- Compliance: Remove accounts as required by data retention policies
Input Parameters
Here are the input parameters required to set up this action:
Mandatory
| Name | Description |
|---|---|
| Distinguished name | The DN of the user to delete |
Here is a sample JSON input:
{
"dn": "cn=john.doe,ou=Users,dc=example,dc=com"
}Response
Upon successful deletion, the action returns:
- HTTP status code
- Confirmation of successful deletion
Users: Reset password
Resets a user's password in Active Directory. The Agent can leverage the skill (workflow), which has been designed to handle password reset requests. Here are some common use cases:
- Help Desk Requests: Reset passwords for locked-out users
- Security Incidents: Force password changes after security events
- New Account Setup: Set initial passwords for new accounts
Input Parameters
Here are the input parameters required to set up this action:
Mandatory
| Name | Description |
|---|---|
| Distinguished name | The DN of the user whose password will be reset |
| Password | The new password to set for the user |
Here is a sample JSON input:
{
"dn": "cn=john.doe,ou=Users,dc=example,dc=com",
"password": "NewSecurePassword123!"
}Response
Upon successful password reset, the action returns:
- HTTP status code
- Operation result status
Groups: Create group
Creates a new group in Active Directory. The Agent can leverage the skill (workflow), which has been designed to create security or distribution groups. Here are some common use cases:
- Project Groups: Create groups for new projects or teams
- Access Control: Set up security groups for resource access
- Distribution Lists: Create email distribution groups
Input Parameters
Here are the input parameters required to set up this action:
Mandatory
| Name | Description |
|---|---|
| Parent distinguished name | The DN of the container where the group will be created |
| Relative distinguished name | The RDN for the new group (e.g., cn=engineering-team) |
Optional
| Name | Description |
|---|---|
| Common Name | The name of the group |
| Group Display Name | The display name for the group |
| Group Name | The group name |
| Email Address | Email address for distribution groups |
| Mail Nickname | Alias for email routing |
| SAM Account Name | Pre-Windows 2000 group name |
| Description | Description of the group |
| Group Type | Security or distribution group type |
| Managed By | DN of the user or group that manages this group |
| Notes | Additional notes about the group |
Here is a sample JSON input:
{
"parentDn": "ou=Groups,dc=example,dc=com",
"rdn": "cn=engineering-team",
"entry": {
"displayName": "Engineering Team",
"description": "Security group for engineering department",
"mail": "[email protected]",
"sAMAccountName": "engineering-team",
"managedBy": "cn=john.doe,ou=Users,dc=example,dc=com"
}
}Response
Upon successful creation, the action returns:
- HTTP status code
- Operation result data
Groups: Search group
Retrieves a list of groups from Active Directory. This action can be leveraged to find groups based on various criteria. Here are some common use cases:
- Group Discovery: Find groups by name or description
- Membership Analysis: Identify groups for access reviews
- Administrative Search: Find groups managed by specific users
Input Parameters
Here are the input parameters required to set up this action:
Optional
| Name | Description |
|---|---|
| Base | The base DN to start the search from |
| Query Planner | Toggle to use the visual query builder (default: enabled) |
| Filter | Raw LDAP filter string (when Query Planner is disabled) |
| Operator | Filter operator type: Equality, Presence, Substring, Greater than equals, Less than equals, Approximate |
| Attribute | The LDAP attribute to search on |
| Value | The value to search for |
| Initial | Initial substring for substring searches |
| Any | Middle substring for substring searches |
| Final | Final substring for substring searches |
Here is a sample JSON input:
{
"base": "ou=Groups,dc=example,dc=com",
"queryPlanner": true,
"filterObject": {
"operator": "SUBSTRING",
"attribute": "cn",
"initial": "engineering",
"any": "",
"final": ""
}
}Response
The action returns a list of group objects, each containing:
- Distinguished Name (DN)
- Group attributes (name, description, members, etc.)
Groups: Modify group
Updates an existing group's attributes in Active Directory. Here are some common use cases:
- Update Properties: Modify group description or display name
- Change Management: Update the group manager
- Email Updates: Modify email addresses for distribution groups
Input Parameters
Here are the input parameters required to set up this action:
Mandatory
| Name | Description |
|---|---|
| Distinguished name | The DN of the group to modify |
Optional
| Name | Description |
|---|---|
| Replace | Array of attributes to replace with new values |
| Add | Array of attributes to add new values to |
| Delete | Array of attributes to remove values from |
Here is a sample JSON input:
{
"dn": "cn=engineering-team,ou=Groups,dc=example,dc=com",
"replace": [
{
"type": "description",
"values": "Updated security group for platform engineering"
}
],
"add": [
{
"type": "mail",
"values": "[email protected]"
}
]
}Response
Upon successful modification, the action returns:
- HTTP status code
- Operation result data
Groups: Delete Group
Deletes an existing group from Active Directory. Here are some common use cases:
- Project Completion: Remove groups when projects end
- Reorganization: Delete obsolete groups during restructuring
- Cleanup: Remove unused or duplicate groups
Input Parameters
Here are the input parameters required to set up this action:
Mandatory
| Name | Description |
|---|---|
| Distinguished name | The DN of the group to delete |
Here is a sample JSON input:
{
"dn": "cn=old-project-team,ou=Groups,dc=example,dc=com"
}Response
Upon successful deletion, the action returns:
- HTTP status code
- Confirmation of successful deletion
Groups: Add members
Adds one or more members to an existing group in Active Directory. Here are some common use cases:
- Onboarding: Add new employees to appropriate groups
- Access Provisioning: Grant access by adding users to security groups
- Team Changes: Add users when they join new teams
Input Parameters
Here are the input parameters required to set up this action:
Mandatory
| Name | Description |
|---|---|
| Group Distinguished name | The DN of the group to add members to |
Optional
| Name | Description |
|---|---|
| Members (Distinguished names) | Array of member DNs to add to the group |
Here is a sample JSON input:
{
"dn": "cn=engineering-team,ou=Groups,dc=example,dc=com",
"members": [
"cn=john.doe,ou=Users,dc=example,dc=com",
"cn=jane.smith,ou=Users,dc=example,dc=com"
]
}Response
Upon successful operation, the action returns:
- HTTP status code
- Operation result data
Groups: Remove members
Removes one or more members from an existing group in Active Directory. Here are some common use cases:
- Offboarding: Remove departing employees from groups
- Access Revocation: Remove access by removing users from security groups
- Team Changes: Remove users when they leave teams
Input Parameters
Here are the input parameters required to set up this action:
Mandatory
| Name | Description |
|---|---|
| Distinguished name (Group) | The DN of the group to remove members from |
Optional
| Name | Description |
|---|---|
| Members (Distinguished names) | Array of member DNs to remove from the group |
Here is a sample JSON input:
{
"dn": "cn=engineering-team,ou=Groups,dc=example,dc=com",
"members": [
"cn=john.doe,ou=Users,dc=example,dc=com"
]
}Response
Upon successful operation, the action returns:
- HTTP status code
- Operation result data
General: Update Distinguished name
Updates the Distinguished Name of an existing directory object, effectively renaming or moving it within the directory tree. Here are some common use cases:
- User Relocation: Move users between Organizational Units during reorganization
- Rename Objects: Rename users or groups when names change
- Directory Restructuring: Reorganize the directory hierarchy
Input Parameters
Here are the input parameters required to set up this action:
Mandatory
| Name | Description |
|---|---|
| Old Distinguished name | The current DN of the object to rename/move |
| New Distinguished name | The new DN for the object |
Here is a sample JSON input:
{
"dn": "cn=john.doe,ou=Engineering,dc=example,dc=com",
"newDn": "cn=john.doe,ou=Platform-Engineering,dc=example,dc=com"
}Response
Upon successful operation, the action returns:
- HTTP status code
- Operation result data
Updated about 2 months ago
