Path-Based Access Control (Connector Filters)
While connectors like SharePoint and Google Drive provide base permissions, they are often too broad. Path-Based Access Control (PBAC) allows Admins to enforce stricter visibility by scanning file paths for keywords and requiring matching User Attributes (e.g., user.country, user.manager) for access.
Logic & Evaluation
The system utilizes OR logic for all permission evaluations, ensuring flexible access across departments.
| Logic Type | Context | Access Rule |
|---|---|---|
| Intra-Attribute | Same Key (e.g., user.country) | User matches if value is IND OR USA. |
| Inter-Attribute | Different Keys | User matches if country rule is met OR manager rule is met. |
Configuration
Path: Settings > General Settings > Article Visibility > Path based access control
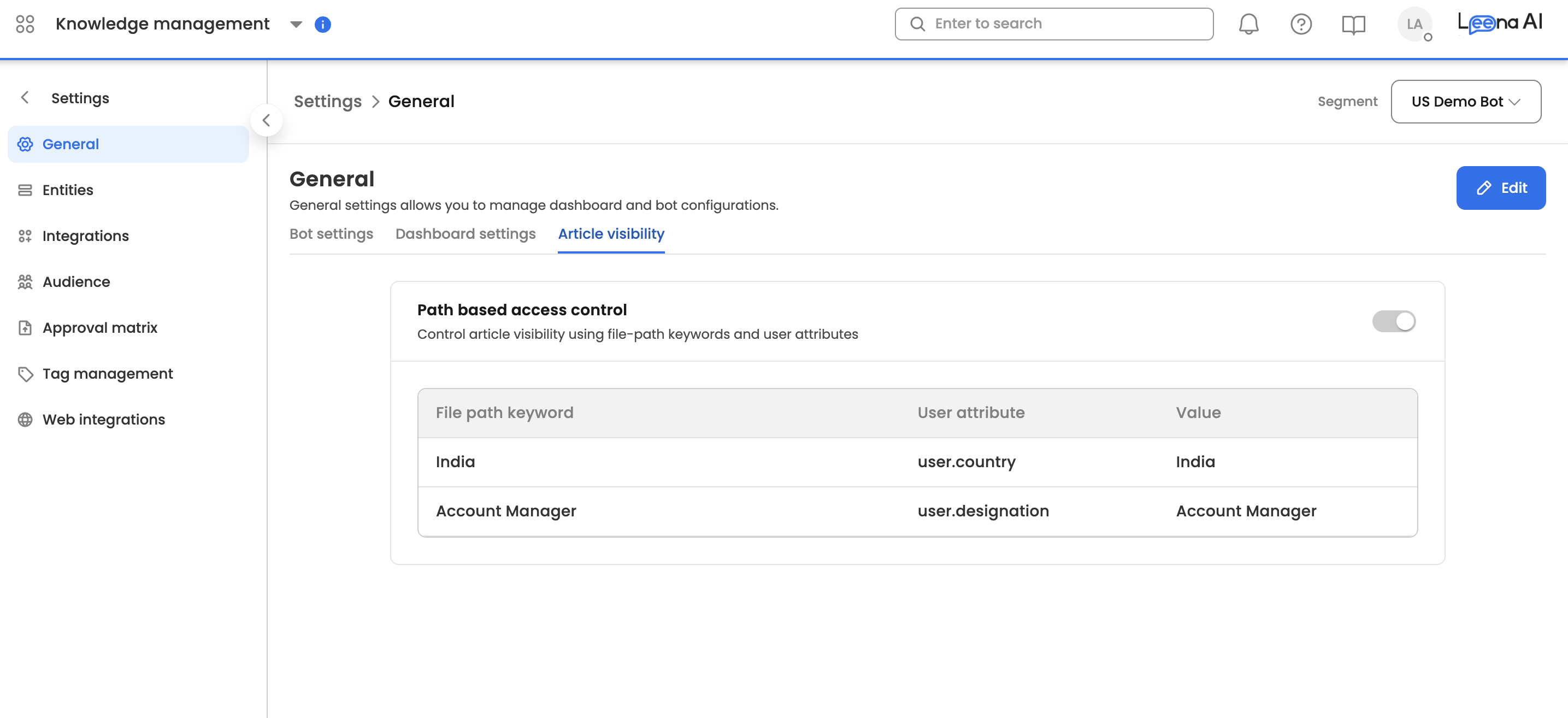
To define a rule, configure the following three components:
- Path Keywords: Multi-value text input (Chips). Define the strings to look for in the file path (e.g.,
Finance,Payroll).
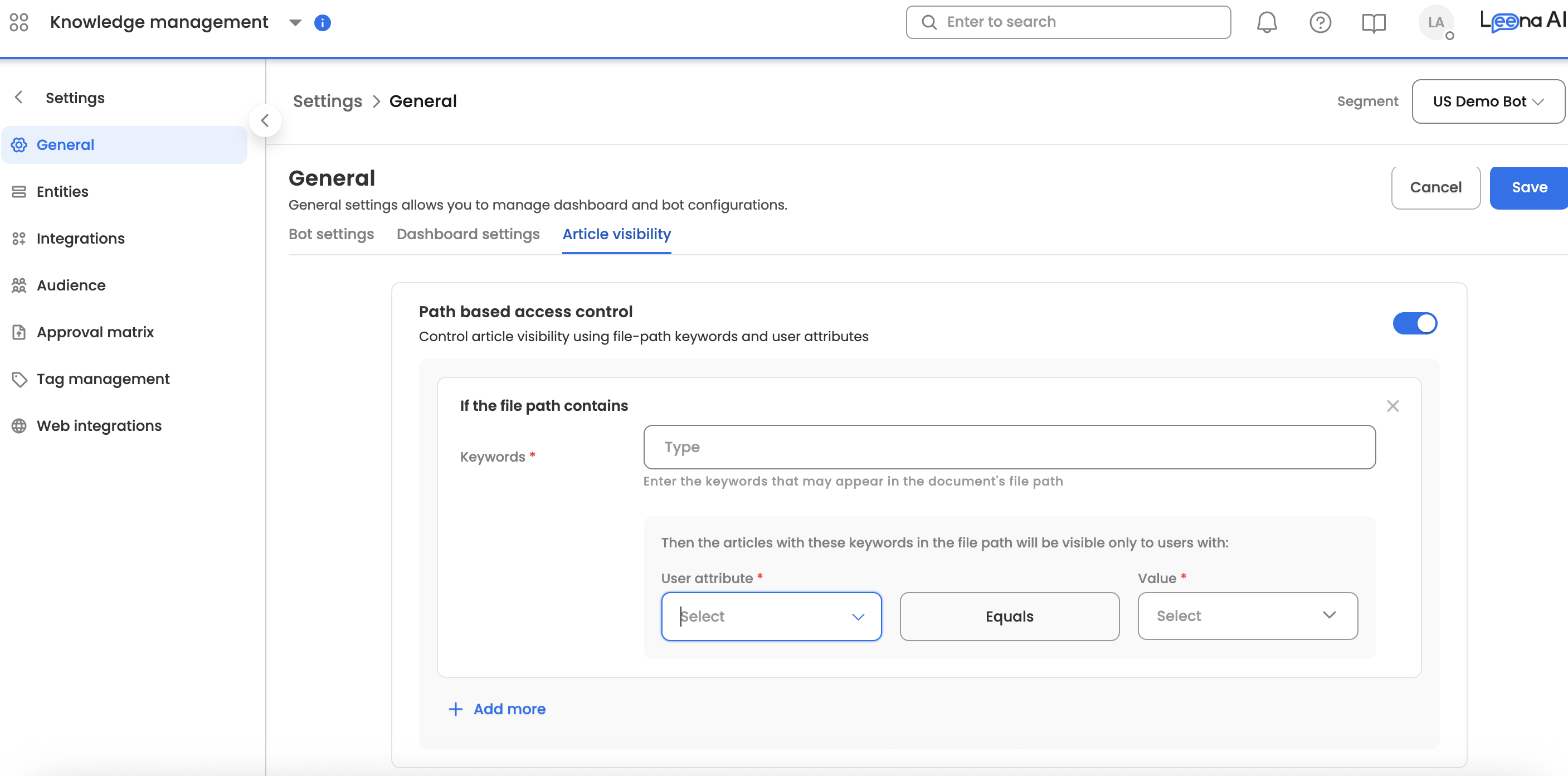
- User Attribute: Single-select dropdown of available user parameters.
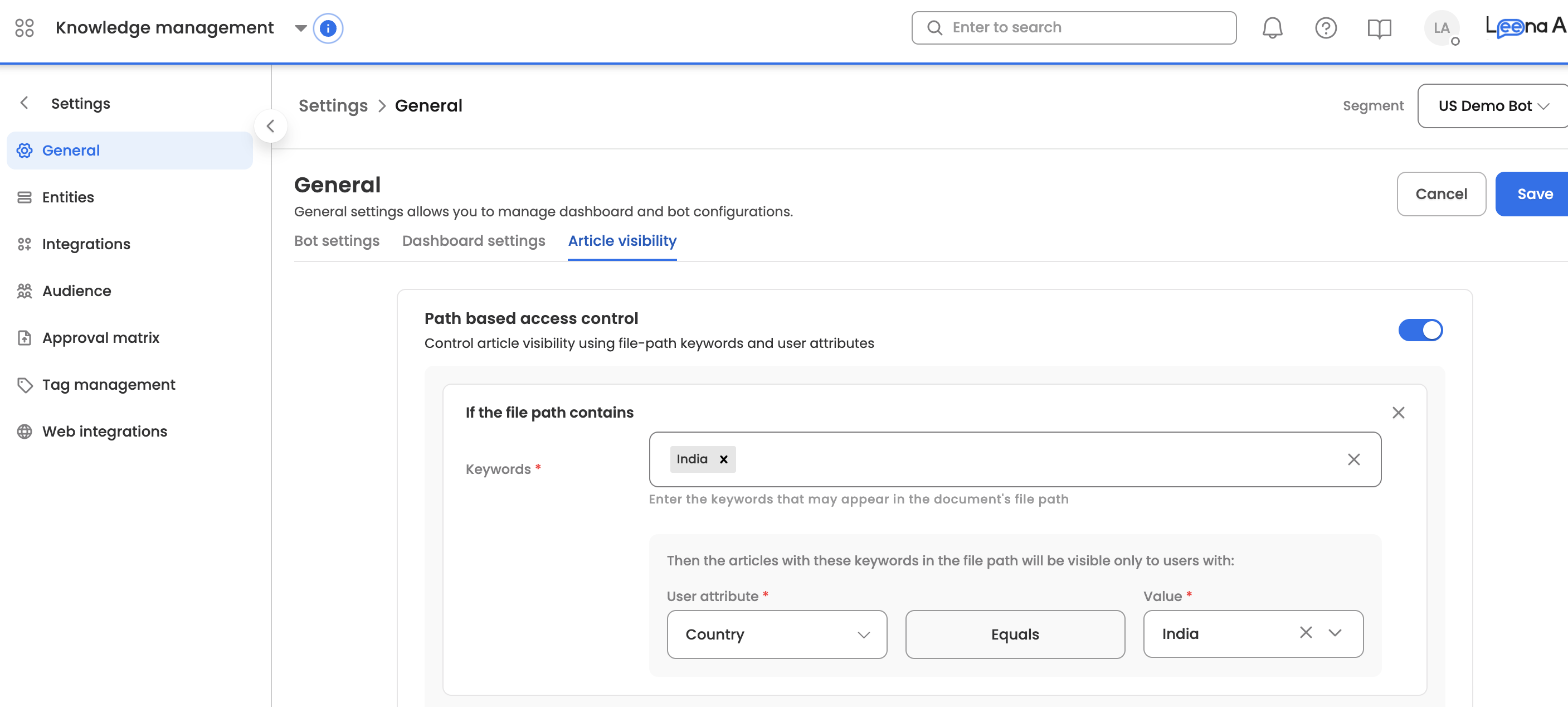
- Required Value: The specific value the user must have to satisfy the filter.
The Sync Process
Permissions are stamped onto articles via a manual sync to ensure high performance at runtime.
- Trigger: Click the Save--->Save and Sync button after modifying rules.
- System State: The configuration page becomes Disabled (Grayed out) during execution.
- Progress: An infobar appears showing "Filters are being applied across your articles. This may take several minutes.".
Environment Behaviour
To maintain architectural consistency, UAT is treated as a downstream mirror of Production.
| Feature | Production (Prod) | UAT / Staging |
|---|---|---|
| Editability | Full (Add/Edit/Delete) | Read-Only (Locked) |
| Sync Action | Enabled | Disabled |
| Article Details | Shows local filters | Shows filters synced from Prod |
Monitoring & Debugging
Article Details Page
Admins can view active filters directly on an article's Details page under the section Path Based Filters.
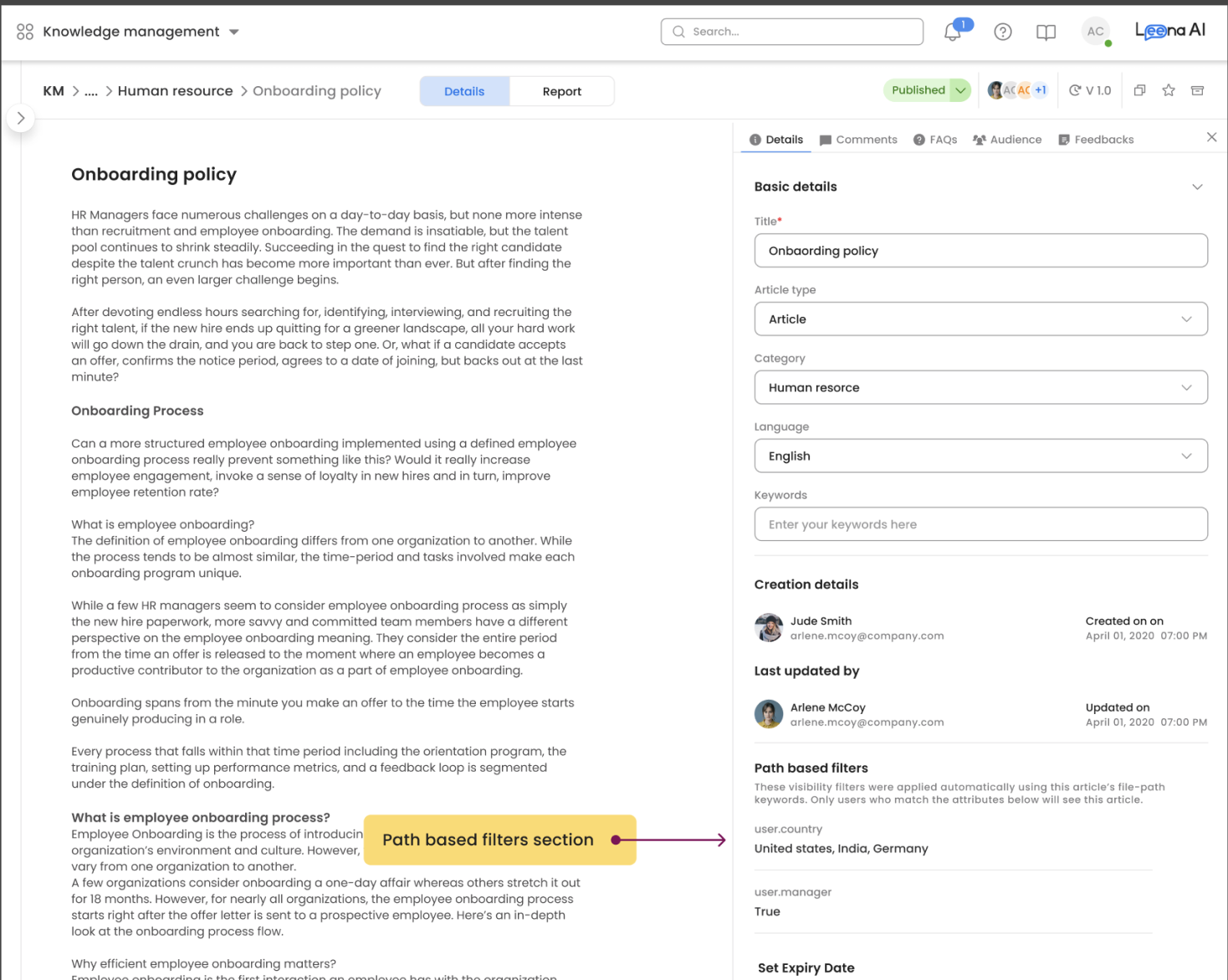
Query Pipeline & Access Control
The final step in the document lifecycle is the enforcement of filters during active user queries. This ensures a closed-loop security system:
When a user submits a query, access is granted only if their user profile parameters satisfy the document's stamped filters. To receive an answer derived from a filtered document, the user's profile must meet all specific criteria. For example, if a document is stamped with:
user.country = India
user.designation = Manager
Only a user whose profile contains both India and Manager will be eligible to retrieve information from that document. This completes the end-to-end security loop, moving from path-based identification to strict runtime enforcement.
Updated 4 days ago
